All news will be posted here
Did you knew - Without hackers
there will be no IEEE 802.11?
Security Blog
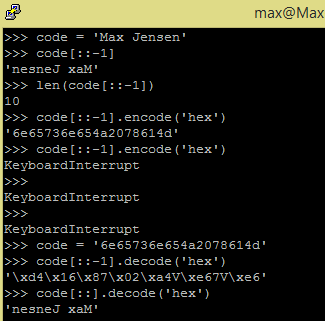
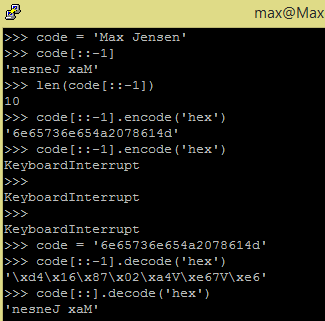
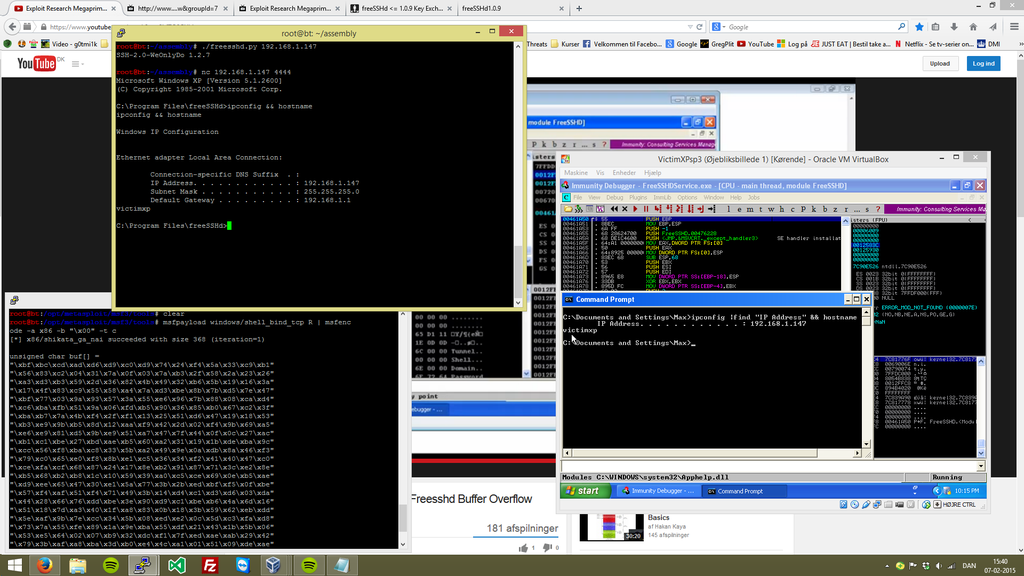
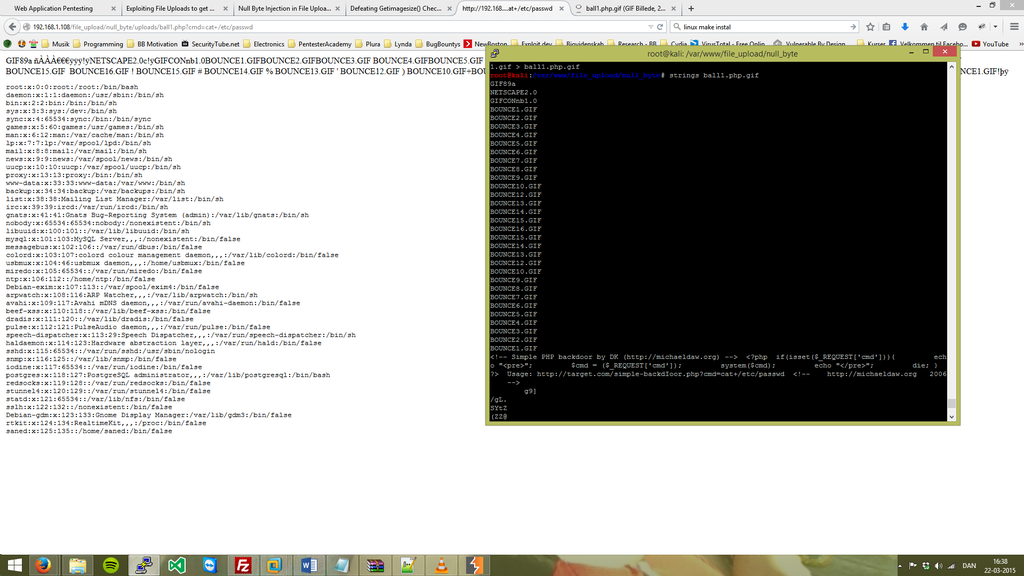
A little experimenting within Backtrack is also a big part of what I'm having fun with, regardless of it's might being going for the root, or just for curiosity of auditing the network. There are many opportunities an malicious attacker can take advantage of such situations, and I'm thinking out side the box, to do something that might are able to preventing such kind of things - by defending my self and surounders!
Familiar with RFID?
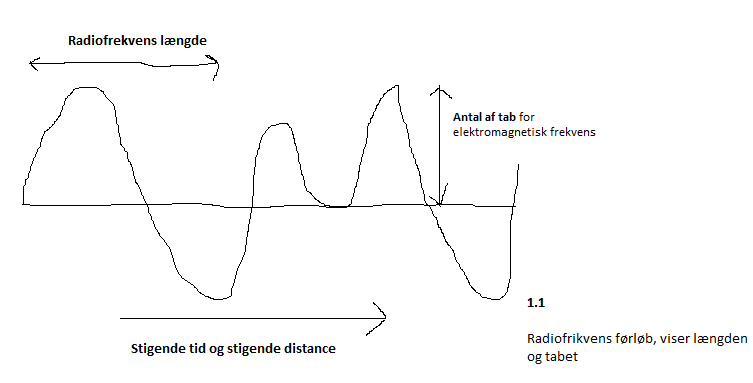
If you want to make some messurements and get a hang on how far your frequences are reaching, then it's also essential to remember where your pointing is at
I'm familiar with RFID, and has been using it to develop my own methods to increase such Things as WiFi length, WiFi Jammer, or even something Ad-hoc.
Being active within IT-security is essential for anyone in the field you and I got might in common. I stay updated with reading books regardless of my interest and curiosity of staying updated all the time. This book is an essential for any person within InfoSec.
I found that Secrets & Lies, provide great prespective on the modern world within Cyber Warfare and so on.
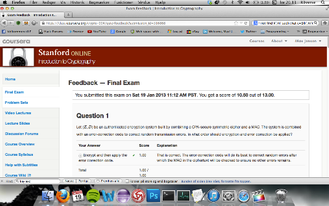
Standford University
Cryptography Course Completed! - Certification by Dan Boneh, Professor at Standford.