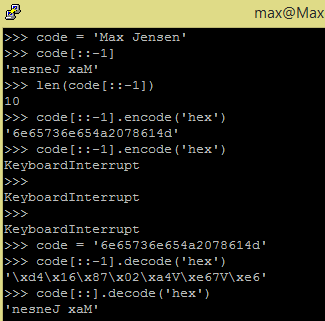
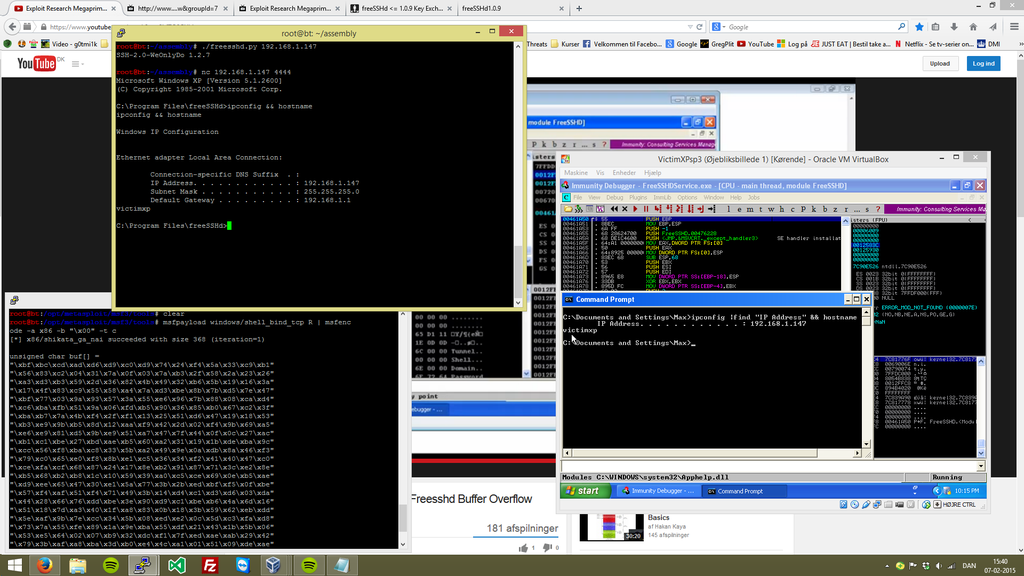
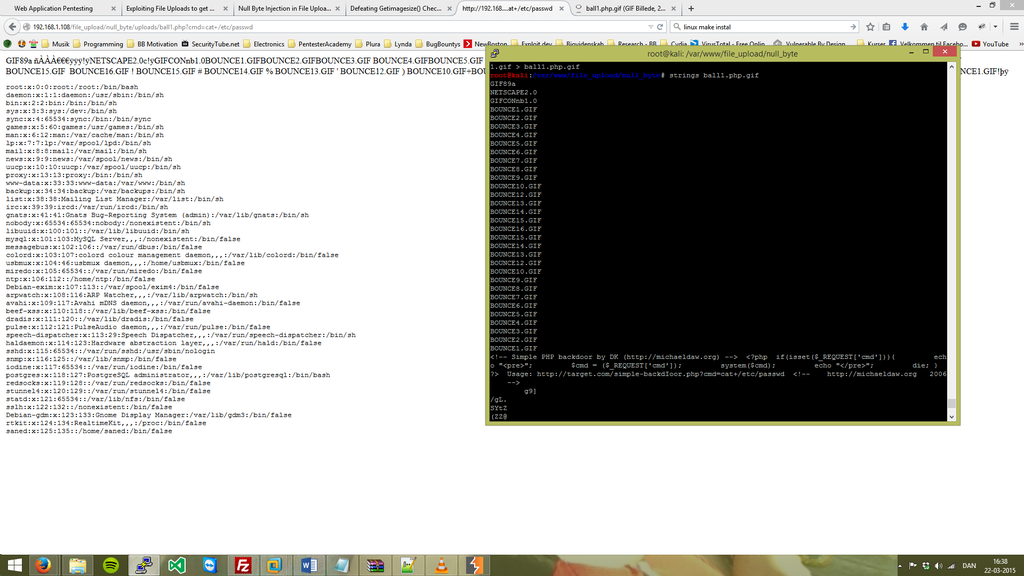
In particular, operating
systems are a huge source of vulnerabilities nowadays..
Security Blog
A wise man once said, give a man a fish, and you feed him for a day. Teach a man to fish, and you feed him for a life time. New Updates is essential to my new Security Blog.
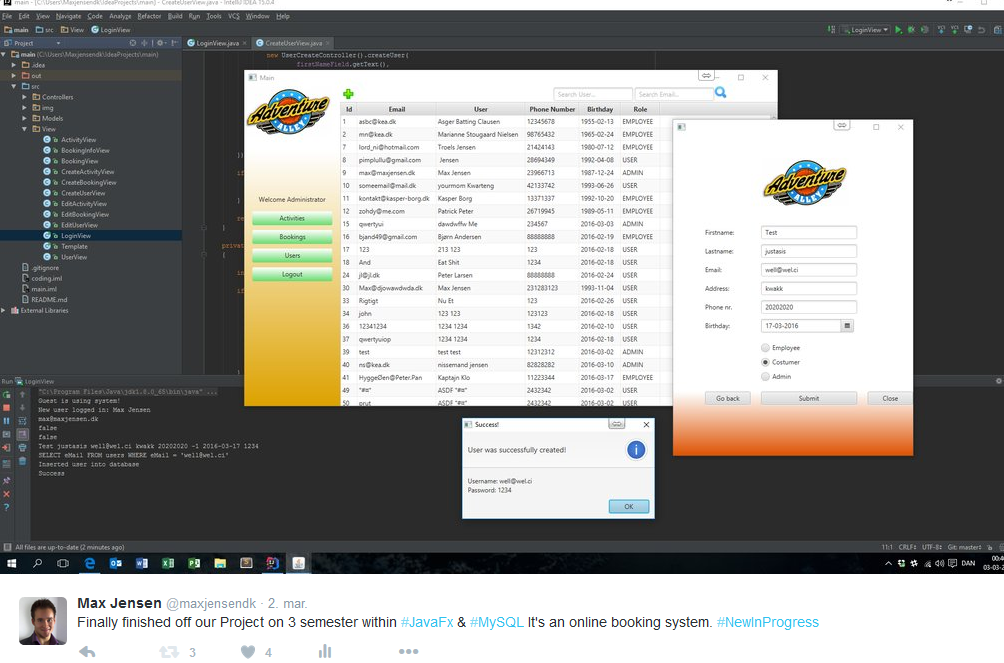
Github - Recent coding
You can follow my currenct projects on GitHub. This is where I post all from Java to C# and all other relevant code that I want to share with the world.