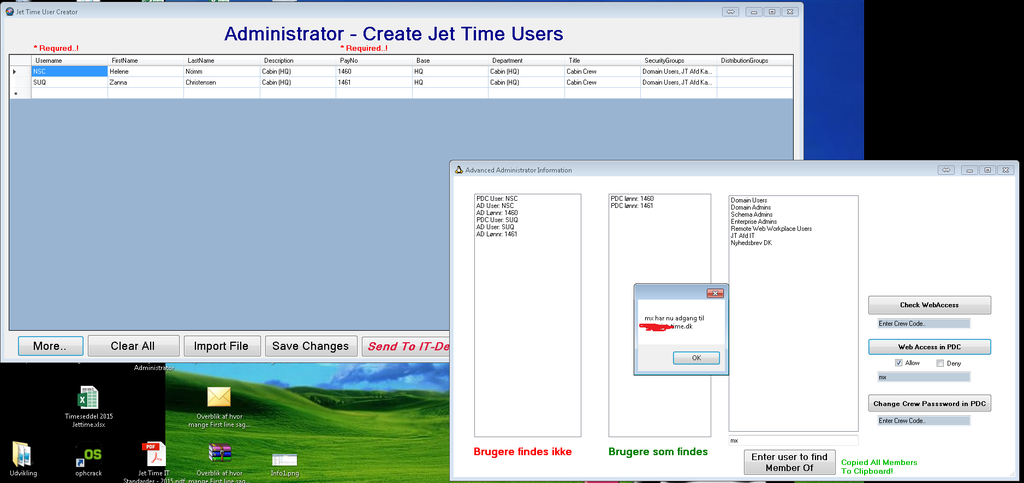
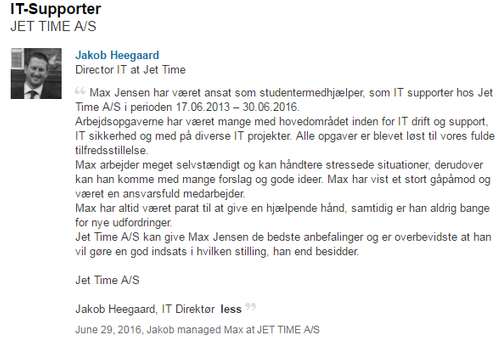
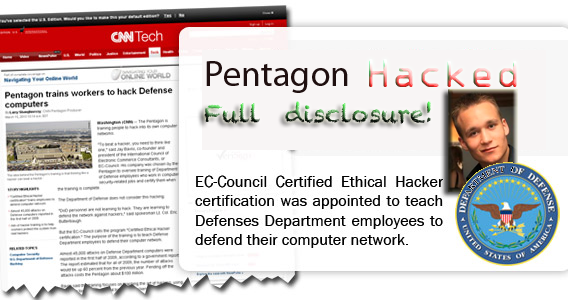
My profile
Key Competences:
- IT Support, IT Consulting & Management
- Executing and Delivering, Result Oriented, Driving Change
- Digital Marketing
- Customer Service
- Contract Management
- Sales & Influence
Specialties:
Business(SMEs), Day Trading, IT Security, Leading & Helping people achieve their goals.
IT Security courses completed:
* x86 Assembly Language and Shellcoding on Linux
* x86_64 Assembly Language and Shellcoding on Linux
* GNU - Debugger Megaprimer
* Exploiting Simple Buffer Overflows on Win32
* Python for pentesters
* Web Application Pentesting
* Javascript for Pentesters
All my certificates from Lynda.com:
http://www.lynda.com/AllCertificates/User/2290141
I'd like to explore new opportunities within IT Security.
If you like to explore further what I'm up to, then follow me on my Twitter page: @Maxjensendk
I am a firm believer in that, no assignment is too big.
Mobile phone: +45 23 96 67 13
Mail: Max@maxjensen.dk
★★★ Alternatives ★★★
✔ Blog: http://www.maxjensens.blogspot.dk
✔ Twitter: http://twitter.com/maxjensendk
✔ Linkedin: http://www.linkedin.com/pub/max-jensen/49/b02/a55
Think of when performing in a new environment:
Don’t be malicious.
Don’t be stupid.
Don’t attack targets without written permission.
Consider the consequences of your actions.
If you do things illegally, you can be caught and put in jail! (Considering in Denmark, Straffeloven § 263 stk. 2)